
Enlarge (credit score: Peach_istock through Getty Photos)
It is not uncommon to listen to information studies about giant information breaches, however what occurs as soon as your private information is stolen? Our analysis reveals that, like most authorized commodities, stolen information merchandise circulate via a provide chain consisting of producers, wholesalers, and shoppers. However this provide chain entails the interconnection of a number of prison organizations working in illicit underground marketplaces.
The stolen information provide chain begins with producers—hackers who exploit susceptible methods and steal delicate data corresponding to bank card numbers, checking account data, and Social Safety numbers. Subsequent, the stolen information is marketed by wholesalers and distributors who promote the info. Lastly, the info is bought by shoppers who use it to commit varied types of fraud, together with fraudulent bank card transactions, id theft, and phishing assaults.
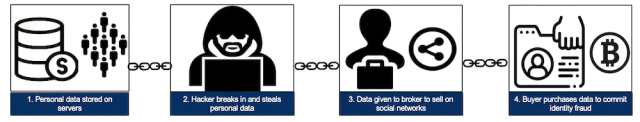
The stolen information provide chain, from information theft to fraud. (credit score: Christian Jordan Howell (CC BY ND))
This trafficking of stolen information between producers, wholesalers, and shoppers is enabled by darknet markets, that are web sites that resemble strange e-commerce web sites however are accessible solely utilizing particular browsers or authorization codes.
Learn 13 remaining paragraphs | Feedback